SQL Injection
1. Browse to target site http://testasp.vulnweb.com/Login.asp 2. Configure Burp proxy, point browser Burp (127.0.0.1:8080) with Burp set to intercept in the proxy tab. 3. Click on the submit button on the login form 4. Burp catches the POST request and waits
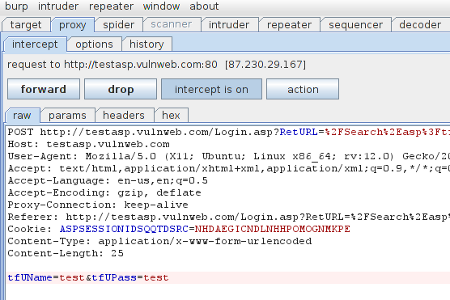
5. Copy the POST request to a text file, I have called it search-test.txt and placed it in the sqlmap directory 6. Run sqlmap as shown here; the option -r tells sqlmap to read the search-test.txt file to get the information to attack in the POST request. -p is the parameter we are attacking.
Another simple test:
Other tests:
POST parameters
You can also attempt to inject parameters passed using POST requests, but you'll need Burp or Firefox tamper to view and edit them. For example, you can test a parameter by adding a ' at the end, like lang=en'.
Bypassing authentication
If you find a poorly-sanitized login page, you can attempt to log in without credentials by injecting the username parameter:
Database enumeration
The exact syntax for injection will vary by database type. In most lab scenarios, the database will be MySQL.
Get version:
You can get the number of columns through trial and error using order by. For each query, increase the column number until the database throws an unknown column error:
Get the current user:
See all tables:
Get column names for a specified table:
Get usernames and passwords (0x3a means :):
You might be able to write to system files depending on permission levels using MySQL's INTO OUTFILE function to create a php shell in the web root:
I suspect you could inject a full reverse shell in there too...
SQLmap
Assuming you've tested a parameter with ' and it is injectable, run SQL map against the URL:
It may not run unless you specify the database type.
Get the databases:
Get the tables in a database:
Get the columns in a table:
Dump a table:
Passing tokens
If the URL isn't accessible, you can pass cookie data or authentication credentials to SQLmap by pasting the post request in a file and using the -r option:
If you just need to pass a cookie:
REST-style URLs
If your URLs have no parameters, you can still test them:
Last updated